Lists of freeware antikeyloggers
Anti-Keyloggers
SpyShelter Personal Free is an "anti-keylogging, anti-spyware program" that "detects and block[s] dangerous and malicious programs". Free version has: System protection (HIPS), AntiKeylogger, AntiScreenCapture and AntiClipboardCapture.
Malwarebytes Anti-Malware Free "The free version of our anti-malware application is designed to clean out all types of malicious malware, including viruses, spyware, trojans, keyloggers, password stealers, dialers and more."»
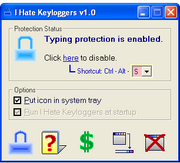
I Hate Keyloggers and MyPlanetSoft's Anti-Keylogger try to thwart keyloggers by deactivating any system-wide hook. This will prevent any existing hook-based keylogger from working. A few rare keyloggers like Martin's Undetectable Keylogger will not be blocked by either of them.
Despite its being "lightweight", there are suggestions of high CPU-usage. Still, given that some online banks encourage and endorse its use, it is definitely worth considering. For Windows, the supported browsers are Internet Explorer, Firefox and Chrome; for Mac, they are Firefox and Safari.»
Some freeware Anti-virus, Anti-spyware, Anti-trojan will detect keyloggers by signatures. Anti-rootkits that detect rootkits using generic methods can only often reveal keyloggers because they can defeat the methods used by keyloggers to hide.
Hardware keyloggers cannot be detected by software methods.
There are different types of software keyloggers, including hooking keyloggers and kernel-driver keyloggers.
Kernel keyloggers are hard to detect and, when they are installed, they can be almost invisible - many are pretty much kernel rootkits. The best defense against kernel keyloggers is to stop them from being installed in the first place by blocking driver-installations using HIPS or limited user accounts..
Hook-based keyloggers can be more easily detected and most of the entries on this page are designed to work against them. Many HIPS also have the ability to block global hooks and, so, will stop hook-based keyloggers as well.
There are other, application-specific keyloggers, most commonly those that target browsers via browser plug-ins (BHOs, extensions) or even proxies for man-in-the-middle attacks.
Anti-Keyloggers
- SpyShelter Personal Free
- MaxSecurity Lab's DataGuard Anti-Keylogger Free (protects against 5 types of keyloggers)
- DewaSoft's KL-Detector v1.3
SpyShelter Personal Free is an "anti-keylogging, anti-spyware program" that "detects and block[s] dangerous and malicious programs". Free version has: System protection (HIPS), AntiKeylogger, AntiScreenCapture and AntiClipboardCapture.
KL-Detector works by trying to detect log files being created by the keylogger. It is probably not very effective except against the most basic keyloggers.
Anti-Spyware/Anti-Malware with Anti-Keylogging
Malwarebytes Anti-Malware Free "The free version of our anti-malware application is designed to clean out all types of malicious malware, including viruses, spyware, trojans, keyloggers, password stealers, dialers and more."»
SUPERAntiSpyware Free "Detect and remove Spyware, Adware, Malware, Trojans, Dialers, Worms,KeyLoggers, HiJackers and many other types of threats."»
BitDefender's QuickScan
BitDefender's QuickScan "is an online tool which uses 'in-the-cloud' scanning to detect malware running on a PC very fast, usually in less than 60 seconds." It is intended as a quick second-opinion check before banking or shopping online.
"QuickScan only detects viruses which are active in memory or present in files that are run at system startup" and it will NOT remove any malware it detects. Supported browsers are: Internet Explorer, Firefox and Chrome.
Other, Passive Methods to Protect against Keylogging (will not detect)
These will not detect any keyloggers if they exist but will make it difficult for them to log valuable data.- DewaSoft's I Hate Keyloggers (nagware)
- QFXSoftware's KeyScrambler Personal (for IE, Firefox & Flock)
- MyPlanetSoft's Anti-Keylogger
- NetworkIntercept's Free Anti-Keylogger (for Internet Explorer)
- MaxSecurity Lab's NextGen Anti-Keylogger Free (for IE, Firefox & Safari)
I Hate Keyloggers and MyPlanetSoft's Anti-Keylogger try to thwart keyloggers by deactivating any system-wide hook. This will prevent any existing hook-based keylogger from working. A few rare keyloggers like Martin's Undetectable Keylogger will not be blocked by either of them.
Free KeyScrambler Personal encrypts users' keystrokes at the kernel-driver level as they enter the computer so that any keylogger planted in the operating system can log only the useless data. KeyScrambler employs advanced key-encryption algorithms and special decryption methods to protect user-inputs in IE, Firefox and Flock.
Free Anti-Keylogger uses NetworkIntercept's Keystroke Interference. This "injects random data" between keystrokes.
Virtual Keyboards
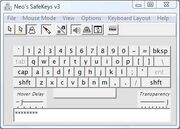
- Neo's SafeKeys
- PlanetSoft's Mouse-Only Keyboard (MOK)
- MiloSoft's Virtual Keyboard
- NetworkIntercept's Virtual Keyboard
- Keylogger Beater (for Firefox)
First off, the free on-screen keyboard offered by Windows XP Accessibility Tools is useless against keyloggers because of its emulation of keystrokes (even in hover mode).
Neo's SafeKeys virtual keyboard launches with unpredictably variable width, height and screen-position to fool mouse-loggers. Passwords are entered into the virtual keyboard with point-and-click or hover mode and, then, inserted into the required password field with drag-and-drop: it does not use the clipboard at all. Version 3 is available and its improvements over version 2 include "great screenlogger protection" and "injection mode" (for those programs that do not allow the preferred "drag and drop").
MyPlanetSoft's Mouse-Only Keyboard (MOK) provides a virtual keyboard with some clipboard-protection and protects against hook-based keyloggers using the same method as MyPlanetSoft's Anti-Keylogger.
Password-Managers
Password-managers are designed to maintain records of password or log-in details securely within encrypted databases, each locked with a master password or a key file. Some password-managers can provide a more secure way of entering log-in details (eg. drag-and-drop) that might thwart keyloggers.
LSN Password Safe is a free password-manager with anti-keylogging measures that can work portably from a USB flash drive. "[It] is easy to use ... with integrated spyware protection. Maximum attention was paid by creation of LSN Password Safe to protect against spyware."
Other, Non-Technological Methods
How to Login from an Internet Cafe without Worrying about Keyloggers observes that you can fool most keyloggers by "alternating between typing the login credentials and typing characters somewhere else in the focus window. For example, type one letter of your password, then click somewhere else within the same focus window (it must be the same window) and type some random characters, then click back in the password area and type the next character, and so on."»
Other similar methods include typing a series of random characters in the form field, highlight them and, then, type the correct information. This will cause the highlighted random characters to be replaced with the valid characters. The idea here is to avoid using the delete key. Or you could assemble your password by cutting and pasting different strings.
Another trick suggested by Ian Richards is to "enter a character by holding down the Alt key and using the numeric keypad. For example the letter 'a' can be entered by ALT 123."»
He also recommends a combination of all these methods to assemble some of the password plus the use of a virtual keyboard like Neo's SafeKeys (portable) for the rest of the password affords even more protection, depending on how frequently screenshots are taken. Copying and pasting passwords from a password-manager to bypass the keyboard might be effective provided there is some protection of the clipboard.
Testing Vulnerability to (Some) Keylogging Methods
Anti-Keylogger Tester (AKLT) is a small (169KB) single-file program that, with its nine tests (7 keylogging & 2 screen-capturing), allows one to check the efficacy of anti-keylogging software.Trusteer's Rapport
Trusteer's Anti-Keylogger Myths argues against the effectiveness of various anti-keylogging measures (virtual keyboards, graphical passwords, password-managers, keystroke-dynamics and even one-time passwords) to conclude that keystroke-encryption as used in its Rapport software provides the strongest defence against keyloggers.
Rapport is a "lightweight security software" intended to provide an extra layer of protection when banking online.Trusteer says: "By locking down customer browsers and creating a tunnel for safe communication with the online website, Rapport prevents Man-in-the-Browser malware and Man-in-the-Middle attacks. Rapport also prevents phishing via website authentication to ensure that account credentials are passed to genuine sources only."»
Despite its being "lightweight", there are suggestions of high CPU-usage. Still, given that some online banks encourage and endorse its use, it is definitely worth considering. For Windows, the supported browsers are Internet Explorer, Firefox and Chrome; for Mac, they are Firefox and Safari.»
And Finally ...
Trusteer's Anti-Keylogger Myths says: "Password managers can be easily bypassed using keyloggers that reside inside the browser ... known as man-in-the-browser malware or malicious browser plug-ins." It adds: "The browser plug-in technology grants the plug-in a lot of privileges, such as full access to the DOM (which is the internal representation of the page currently displayed), and subscription to browser events (such as 'navigation', 'page load' and 'form submission'). This makes it very easy for a malicious plug-in to get hold of the credentials."
One might then infer a rather simple and straightforward precautionary measure against man-in-the-browser attacks: for general surfing, use your favourite browser with all your favourite plug-ins/add-ons/extensions/BHOs; for security-critical purposes such as online-shopping and -banking, use a different, portable browser (eg. Firefox, Iron,Opera, QtWeb) with an absolute minimum of trusted plug-ins installed and enabled (and, of course, maintain the security of the browser and any such plug-ins by keeping them updated to the latest versions).
Resources to learn about keylogging and antikeylogging
- Introduction to Spyware Keyloggers - http://www.securityfocus.com/infocus/1829
- How to Login from an Internet Cafe without Worrying about Keyloggers -http://cups.cs.cmu.edu/soups/2006/posters/herley-poster_abstract.pdf
- Keyloggers: How They Work and How to Detect Them - http://www.viruslist.com/en/analysis?pubid=204791931
- Sandboxie and Keyloggers - http://www.sandboxie.com/index.php?DetectingKeyLoggers
- Trusteer's Anti-Keylogger Myths - http://www.trusteer.com/sites/default/files/Anti_Keylogger_Myths.pdf


 Added by
Added by 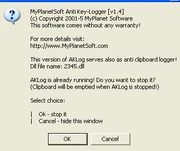
 Added by
Added by 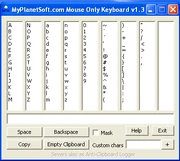
No comments:
Post a Comment